In the world of cybersecurity, Capture the Flag (CTF) competitions are a big deal. Whether you’re new to the field, a seasoned expert, or just a curious enthusiast, you’ve likely come across CTFs. Maybe you’ve already competed in one or plan to join someday.

If you ask us, that sounds like a fantastic idea! Of course, before you dive in, it’s good to know which CTF format suits you best. Luckily, there are only two main types: Jeopardy and Attack & Defense.
But why these two? How did they come about? What are the pros and cons?
Fret not! We’ve put together a brief history and a handy comparison to help you understand each format’s importance and choose the one that best fits your skills and interests.
A short introduction to Capture the Flag (CTF) competitions
CTF competitions have long been a vital component of cybersecurity training. While the thrill of winning and the allure of prizes are exciting, the true value of CTFs extends far beyond the contest experience.
CTFs are designed to test and enhance participants’ abilities across various domains of computer security. Through hands-on challenges, participants gain practical experience in critical areas such as cryptography, reverse engineering, web security, and network analysis. By simulating real-world scenarios, CTFs provide a platform where individuals or teams tackle complex problems, putting their technical skills and analytical prowess to the test. Ultimately, these competitions prepare them for potential cybersecurity threats.
To more accurately reflect real-world scenarios and test a broader range of skills, CTFs have evolved into two main formats: Jeopardy-style, which features a range of categorized challenges, and Attack & Defense, where teams defend their own systems while attacking their opponents’ systems.
The first Jeopardy-style CTF was organized in 2000 by the DEF CON hacking conference in Las Vegas. Since then, Jeopardy-style CTFs have gained significant popularity, with events like DEF CON CTF attracting participants from around the globe. For example, the DEF CON CTF Qualifier 2020 saw over 1,300 teams from various countries compete online. In 2022, DefCamp’s D-CTF 21-22 brought together over 1,000 teams and more than 3,000 players from 96 countries, all competing in a fully online format.
Over time, the Attack & Defense format evolved and gained popularity too, adding excitement to competitions. It made a notable impact at events like the European Cyber Security Challenge in the past years and it was also embraced by events like the National Cybersecurity Challenge, which precedes the European Cyber Security Challenge, or even by DefCamp’s D-CTF, starting 2022.

What is Jeopardy-style CTF?
Definition and structure of Jeopardy CTFs
Jeopardy-style CTFs are a type of cybersecurity competition where participants face a series of challenges categorized into different topics. Each challenge is associated with a specific point value, and teams or individuals earn points by solving these challenges.
Typical formats of Jeopardy-style CTFs include a range of categories such as:
- Web security (or Web Exploitation or Web App Security): challenges in this category focus on vulnerabilities and security issues related to web applications. Participants might need to exploit flaws in web code or configurations, such as SQL injection, cross-site scripting (XSS), or cross-site request forgery (CSRF).
- Cryptography (or Crypto): this category deals with challenges related to cryptographic algorithms and protocols. Participants might need to break encrypted messages, decipher encoded texts, or understand cryptographic principles to solve problems.
- Forensics (or Digital Forensics or Data Recovery): forensics challenges involve analyzing digital evidence to uncover hidden information or reconstruct events. This can include examining files, disk images, network traffic, or memory dumps.
- Reverse engineering (or RE or Binary Analysis): this category involves analyzing and deconstructing software to understand its behavior, discover vulnerabilities, or uncover hidden functionality. Participants might work with binaries, software code, or obfuscated files.
- Binary exploitation (or Pwn): challenges in binary exploitation focus on finding and exploiting vulnerabilities in compiled binary programs. This often involves techniques like buffer overflow attacks, format string vulnerabilities, or exploitation of faulty memory management.
- Networking (or Network Security or Network Exploitation): networking challenges involve understanding and manipulating network protocols and traffic. Participants may need to analyze network packets, exploit network vulnerabilities, or reconstruct network traffic.
- Steganography (or Stego): steganography challenges involve hiding data within other data, such as embedding secret messages within images, audio files, or text. Participants need to detect and extract these hidden messages.
- Programming (or Code Challenges or Script Writing): this category includes a variety of challenges that don’t fit neatly into the other categories. It might cover unique or novel problem types, puzzles, or general cybersecurity knowledge.
- Miscellaneous/General (or MISC, Other, Various, or Mixed): programming challenges require writing code to solve problems or exploit vulnerabilities. This can involve creating scripts, developing custom tools, or solving algorithmic problems.
Spoiler alert: you’ll find such challenges, for free, on the CyberEDU platform (as shown in the image below).
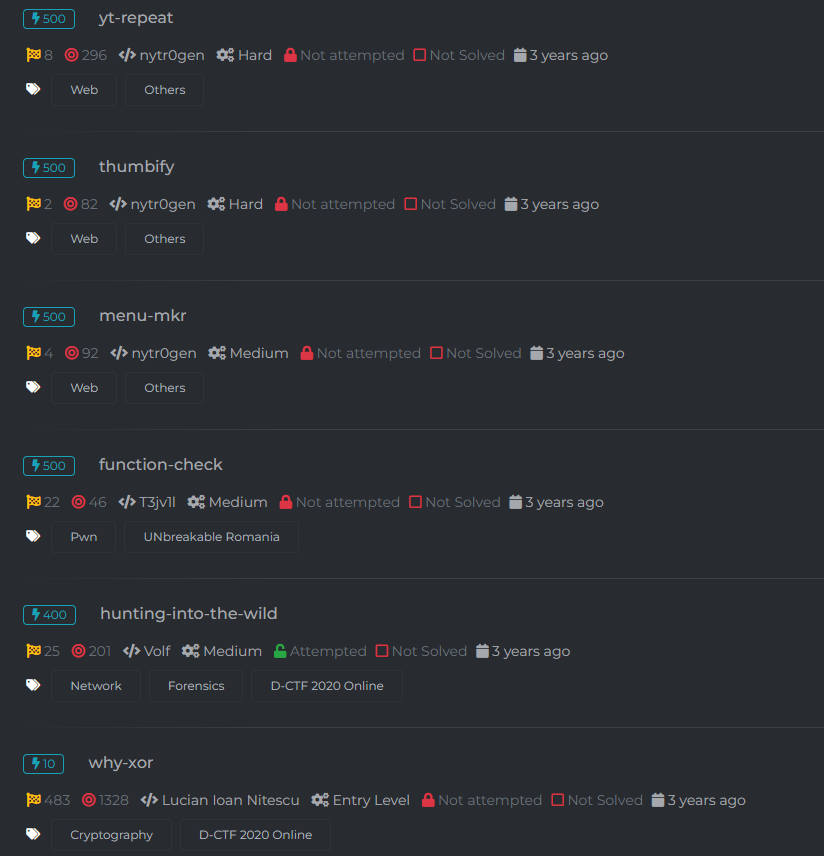
What are the gameplay mechanics of Jeopardy CTFs?
In a Jeopardy-style CTF, players or teams choose challenges from a board or list, each assigned a point value based on difficulty. The goal is to solve these challenges to accumulate the highest number of points.
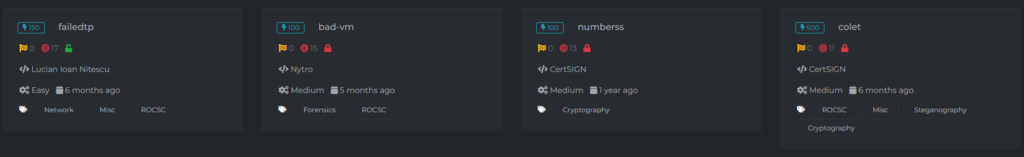
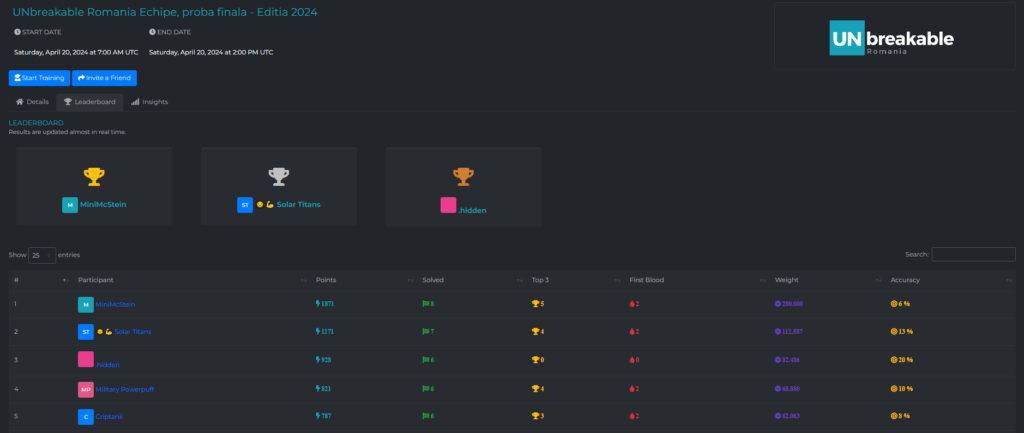

To solve these challenges, players use a combination of technical skills, analytical thinking, and creativity. Each successful solution earns points, and the team or individual with the most points at the end of the competition is declared the winner.
What are the skills required (and/or acquired) in Jeopardy CTFs?
Participating in a Jeopardy-style CTF typically requires – and also helps you acquire or refine – a diverse set of skills:
- Problem-solving: participants approach complex problems systematically and creatively.
- Technical knowledge: participants explore various cybersecurity domains such as cryptography, web security, and reverse engineering.
- Analytical skills: participants get to dissect problems and identify patterns or solutions.
- Hands-on experience: participants get to practice with tools and techniques relevant to the challenges.
- Teamwork: many Jeopardy CTFs involve team-based challenges, which involve the ability to collaborate effectively with others, share knowledge, and coordinate efforts to solve complex problems.
- Time management: CTFs are often time-constrained, which means participants need to manage their time efficiently, prioritize tasks, and work under pressure.
- Adaptability: participants need to adapt quickly to new problems and learn new skills on the fly, enhancing their overall ability to handle unforeseen issues.
- Persistence and resilience: working through difficult problems and sometimes failing before succeeding involves persistence and resilience.
Pros vs Cons for Jeopardy CTFs
Pros of Jeopardy CTFs:
Jeopardy-style CTFs offer a well-structured approach to cybersecurity competitions, with several advantages that make them appealing and efficient:
- Focus on individual skills: Jeopardy-style CTFs allow participants to showcase their expertise in specific areas.
- Easier to organize: since challenges are predefined and categorized, these events can be simpler to set up compared to other formats.
- Scalable: the format can accommodate varying numbers of participants, from small groups to large teams, making it versatile.
Cons of Jeopardy CTFs:
At the other end of the spectrum, Jeopardy-style CTFs come with certain drawbacks that may impact the participant’s learning experience:
- Less emphasis on real-world scenarios: while educational, the challenges may not fully replicate the complexity of real-world cybersecurity incidents.
- Can become repetitive: without constant updates and new challenges, the format may become monotonous for participants who regularly engage in similar competitions.
Now that we’ve built a solid understanding of Jeopardy-style competitions, let’s move onto the Attack & Defense format, to explore how this format offers a different approach to testing and developing cybersecurity skills.
What are Attack & Defense CTFs?
Definition and structure of Attack & Defense CTFs
As compared to the more structured and challenge-based Jeopardy type CTFs, Attack & Defense CTFs offer a dynamic and interactive approach to cybersecurity competitions. In this format, teams have to defend their own infrastructure while simultaneously attacking the other teams’ systems. This setup closely mimics real-world cyber warfare, where defense and offense are equally critical.

Typical formats of Attack & Defense CTFs involve each team being given a vulnerable system or network to protect. Throughout the competition, they must patch vulnerabilities, maintain service availability, and fend off attacks from opponents. Simultaneously, they must identify and exploit vulnerabilities in the systems of competing teams to score points.
What are the gameplay mechanics of Attack & Defense CTFs?
In an Attack & Defense CTF, teams earn points through both offensive and defensive actions.
Here are some examples of:
- Offensive tasks: scanning for vulnerabilities in opponents’ systems, exploiting weaknesses, and capturing flags from compromised systems.
- Defensive tasks: patching vulnerabilities, monitoring network traffic for malicious activity, configuring firewalls, and ensuring system uptime.
Maximum points are scored by successfully completing both types of tasks: compromising other teams’ systems, capturing their flags, and maintaining the security and functionality of their own systems.
And, to do that, teams must balance their resources and strategies between defense and offense, making the gameplay dynamic and complex – and, we dare say, way more fun.
What are the skills required in Attack & Defense CTFs
Participating in an Attack & Defense CTF typically requires – and also improves – a broad set of skills:
- System administration: managing and configuring systems to ensure they are secure and resilient against attacks.
- Network security: implementing and maintaining network protections, such as firewalls and intrusion detection systems, to defend against network-based threats.
- Offensive tactics: crafting and executing strategies to exploit vulnerabilities in opponents’ systems, requiring knowledge of exploits and attack vectors.
- Incident response: reacting to and mitigating the effects of attacks on your own infrastructure, including analyzing and addressing security breaches.
- Strategic thinking: developing and executing both offensive and defensive strategies to outmaneuver opponents and maintain system integrity.
- Teamwork and communication: coordinating with team members to manage defense and attack efforts effectively, sharing information and strategies to adapt to evolving challenges.
Pros vs Cons for Attack & Defense CTFs
Pros of Attack & Defense CTFs
As mentioned before, Attack & Defense CTFs competitions are designed to simulate real-world cyber warfare, providing participants with a realistic and immersive experience, with key advantages being:
- Real-world applicability: Attack & Defense CTFs are highly relevant to actual cybersecurity challenges as they immerse participants in scenarios that closely resemble real-world cyber incidents. Teams must not only defend their own systems but also actively seek out and exploit vulnerabilities in their opponents’ infrastructure. This is a more hands-on experience that helps participants develop practical skills and a deeper understanding of how offensive and defensive tactics are applied in real-life situations.
- Teamwork and communication: effective coordination is essential for balancing offensive and defensive tasks, managing resources, and responding to threats in real time. Participants learn to communicate effectively under pressure, delegate tasks, and work together to achieve common goals. These soft skills are crucial for success in real-world cybersecurity roles, where teamwork and clear communication are often key to addressing complex security challenges.
- Dynamic learning environment: teams must adapt their strategies based on the actions of their opponents. This encourages participants to innovate and apply their knowledge in more challenging ways.
- Comprehensive skill development: teams gain experience in a wider range of skills – not just a specific one, such as system administration, network security, incident response, and offensive tactics.
- Competitive edge: employers value hands-on experience that demonstrates the ability to handle real-world security challenges. So, being successful or even participating in an Attack & Defense CTF can serve as strong proof to a resume or professional portfolio.
Cons of Attack & Defense CTFs
Where there are benefits, there are also challenges. Here’s what goes for Attack & Defense CTFs:
- More complex to organize: each team needs to have its own isolated infrastructure, which means creating multiple vulnerable systems that participants can attack and defend. Additionally, organizers must ensure a balanced environment where all teams have an equal chance to succeed. This also involves continuous monitoring throughout the event to maintain functionality.
- Requires more resources and setup: such events typically require significant amounts of hardware, software, and technical expertise to set up and maintain. The competition environment must be robust and capable of handling numerous simultaneous attacks and defenses. Organizers need to invest resources into configuring systems, setting up network infrastructure, and ensuring that the technical support is in place to handle any issues that arise.
- Higher technical expertise needed: the organizers need to design and deploy complex systems and anticipate potential security challenges and vulnerabilities.
This is a more detailed topic that you might have expected. So let’s try to tone this down, by summarizing key differences between Jeopardy and Attack & Defense, for a clearer comparison.
Key differences between Jeopardy and Attack & Defense CTFs
When choosing between Jeopardy-style and Attack & Defense Capture the Flag (CTF) competitions, understanding their core differences can help you decide which format best suits your skills and goals.
The following table highlights the key distinctions between these two popular CTF formats, providing insights into their focus, gameplay dynamics, learning outcomes, and community engagement.
| Aspect | Jeopardy-Style CTFs | Attack & Defense CTFs |
| Focus and objectives | Puzzle-solving and knowledge testing | Real-world simulation and strategic thinking |
| Gameplay experience | Solo vs team play dynamics: individual or small teams Intensity of real-time interactions: generally less intense; participants work at their own pace | Solo vs team play dynamics: team-based; requires close collaboration Intensity of real-time interactions: highly dynamic and intense with real-time interactions |
| Learning outcomes | Specific technical skills and theoretical knowledge | Practical skills, teamwork, and adaptability |
| Community and networking | Opportunities for collaboration and networking are less emphasized | Extensive community interaction and networking opportunities |
Choosing the right CTF format for you
Selecting the ideal Capture the Flag (CTF) format can significantly impact your learning experience and overall success in cybersecurity competitions. The right choice depends on various factors, such as:
Skill level and experience
- Beginners: if you’re new to cybersecurity, Jeopardy-style CTFs might be a better fit, because you can enjoy a structured environment with challenges categorized by difficulty, making it easier to gradually build your skills in different areas of cybersecurity.
- Intermediate: those with some experience may find Attack & Defense CTFs more engaging due to their more complex and dynamic environment, where you can apply your knowledge in practical scenarios and develop advanced strategies.
- Advanced: why not do both? For seasoned professionals, Attack & Defense CTFs offer the opportunity to tackle real-world simulations that demand high-level skills and team coordination. In the same vein, Jeopardy-style CTFs can also be valuable for refining specific technical abilities or preparing for specialized certifications.
Personal and professional goals
- Personal goals: if you prefer solving individual challenges and learning through structured problems, Jeopardy-style CTFs may be the answer. If you’re excited by the challenge of managing both offense and defense in a competitive environment, go for Attack & Defense CTFs.
- Professional goals: if your goal is to gain hands-on experience in real-world scenarios, Attack & Defense CTFs can provide more practical insights. On the other hand, if you’re focused on building foundational knowledge or preparing for certifications, Jeopardy-style CTFs can help you hone specific skills.
Resources
- Time and effort: Jeopardy-style CTFs require less preparation and can be more flexible, making them suitable for those with limited time. Attack & Defense demands a more extensive setup and ongoing involvement, so ensure you have the time to fully engage.
- Team availability: Attack & Defense CTFs are team-based and require collaboration. If you have a strong team or are willing to form one, these competitions can provide a richer experience. Conversely, Jeopardy-style CTFs can often be tackled solo or with a smaller team.

At the end of the day, there’s no right or wrong choice—it’s all about what fits your personal goals and interests. Both Jeopardy and Attack & Defense CTFs are vital for any cybersecurity enthusiast or professional, each offering unique benefits. Embracing both types will help you build a well-rounded skill set and comprehensive knowledge.
CyberEDU is well-equipped to support your participation in these activities.
Whether through third-party events, our own public CTFs, or customized events tailored for your company, we provide the ideal platform for honing your skills.
Over the years, we have successfully hosted numerous Jeopardy and Attack & Defense CTFs, celebrating the achievements of many satisfied participants.



You could be in one of our future pictures.







